Crypto Key Lifecycle
The following publications provide general key management guidance. A crypto period is the operational life of a key and is determined by a number of factors based on.

What Is A Cryptographic Key Management System The Security Lifecycle Solution Mtg Ag
Best Practice for Lifecycle Crypto Key Management Associations using cryptography for getting private data have the decision of equipment and programming put together arrangements depending with respect to the idea of the information needing encryption.

Crypto key lifecycle. Centralized transparent key management. Encryption Key Management is the management of cryptographic keys in the cryptosystem. Key Managers focus on the governance of keys as they move through the key lifecycle from creation to activation and use to revocation and destruction.
Protection of the encryption keys includes limiting access to the keys physically logically and through userrole access. This is commonly referred to as key rollover A newly generated key is often stored in the key repository along with the old keys. Good key management entails 10 simple yet necessary steps which will ensure that you will be able to gain access to your data or communications in a secure manner when you need it.
Keys have a life cycle. Key generation key. Preactivation active suspended deactivated compromised destroyed destroyed compromised and revoked.
Cryptography Inventory - Best Practice Tips. The term lifecycle refers to the creation use and deactivation of a cryptographic module. A single item of keying.
The typical encryption key lifecycle likely includes the following phases. Key Management Lifecycle Key Management Lifecycle Cryptographic key management encompasses the entire lifecycle of cryptographic keys and other keying material. Basic key management guidance is provided in SP800-21.
Set to Draft initially during configuration. Key creation must be conducted in a secure environment hardened system and may include the need to conform to requirements for separation of duties. Recommendation for Key Management SP 800-57 Part 1 Revision 5 - General This Recommendation provides cryptographic key-management guidance.
In most cases the key generated will be a symmetric key aka. It consists of three parts. Key Managers expand full lifecycle of the cryptosystem keys to include protection storage exchange replacement and use of keys.
EKM and Hardware Security Modules HSM. Expired keys can be kept and used for verifying authenticated or signed data and decryption but they cannot be used to create new authentication codes signatures or encrypt data. Encryption key management is administering the full lifecycle of cryptographic keys.
Since placing a key in a distributed repository is not an atomic operation the new cryptographic key initially becomes available. The task of key management is the complete set of operations necessary to create maintain protect and control the use of cryptographic keys. Therefore a robust key management system is important and policies must include the following.
When using the module set this field to. An encryption key goes through a number of possible stages during its lifecycle. What is Cryptographic Inventory.
IBM Security Guardium Key Lifecycle Manager helps customers meet regulations such as the Payment Card Industry Data Security Standard PCI DSS Sarbanes-Oxley and the Health Insurance Portability and Accountability Act HIPAA by providing centralized management of encryption keys. Unlike vault combinations however encryption algorithms can be changed. Signature verification key Secret authentication key Public authentication key Long term data encryption Key.
The National Institute of Standards and Technology NIST provides strict guidelines for most aspects of the life-cycle of cryptographic keys and has also defined some standards on how a crypto period is determined for each key. 32 Key Lifecycle Management Key lifecycle management refers to the creation and retirement of cryptographic keys. Theyre created live useful lives and are retired.
The first step in the key management lifecycle is to generate the key. What is the Encryption Key Management Lifecycle. Most Enterprise Key Managers utilize KMIP.
Key management and security also serves as the linchpin for all other encryption systems and tools within an organization. Part 1 provides general guidance and best practices for the management of cryptographic keying material including definitions of the. Crypto module lifecycle state.
Scalable encryption key management also improves key lifecycle management which prevents unauthorized access or key loss which can leave data vulnerable or inaccessible respectively. Key management concerns itself with keys at the user level either between user or system. Key lifecycle can be managed by setting key status to currently active to future effective key or to expired.
The National Institute of Standards and Technology identifies the stages as. Crypto Agility 2 Cryptographic Vulnerabilities 7 Cryptography 65 Cryptography Inventory 5 Cryptosense Company News 18 Encryption 6 HSM Security 7 Key Lifecycle Visibility 4 Other 7 Products 24 Security 82 Tech 10 Most Popular Posts. It must be created used possibly changed and eventually disposed of.
What is encryption key management. This means that encryption keys tend to proliferate as they pass through a life cycle of generation active use retirement deletion and replacement. Generating using storing archiving and deleting of keys.
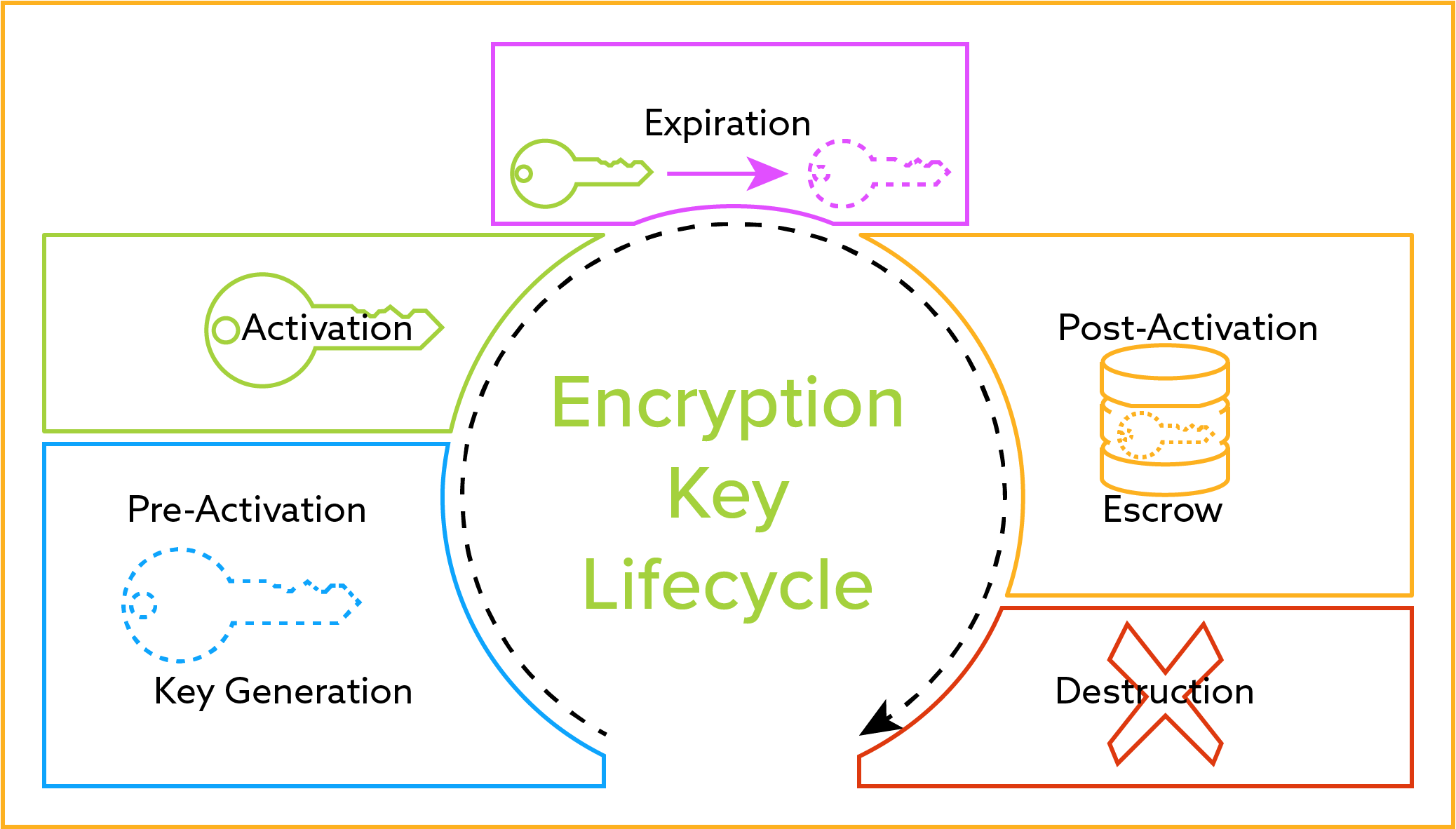
Designing Applications For Encryption Key Management

Encryption Key Management System Prime Factors
.png)
The Private Life Of Private Keys

Identity And Credential Lifecycle Cloud Data Multi Factor Authentication Cyber Security

Decentralized Ai In 5 Minutes Blockchain Cryptocurrency Technology Trends Blockchain Technology
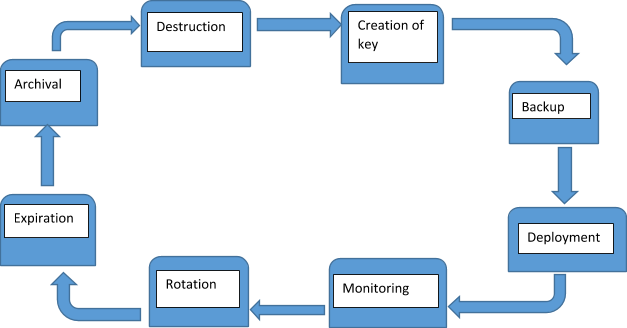
Introducing A Pci Dss Compliant Key Management System To A Bank
The Key Management Lifecycle The Falcon S View

Blockchain Project Development Lifecycle Development Life Cycle Blockchain Life Cycles

Exploring The Lifecycle Of A Cryptographic Key
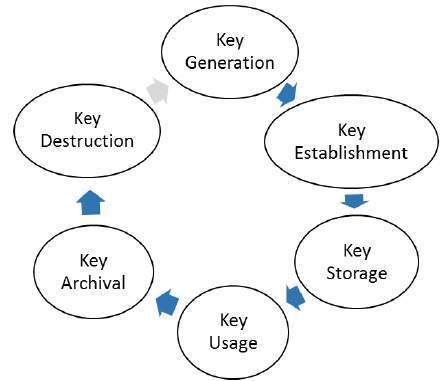
Public Key Infrastructure Tutorialspoint

How You Should Approach The Secure Development Lifecycle Dataversity
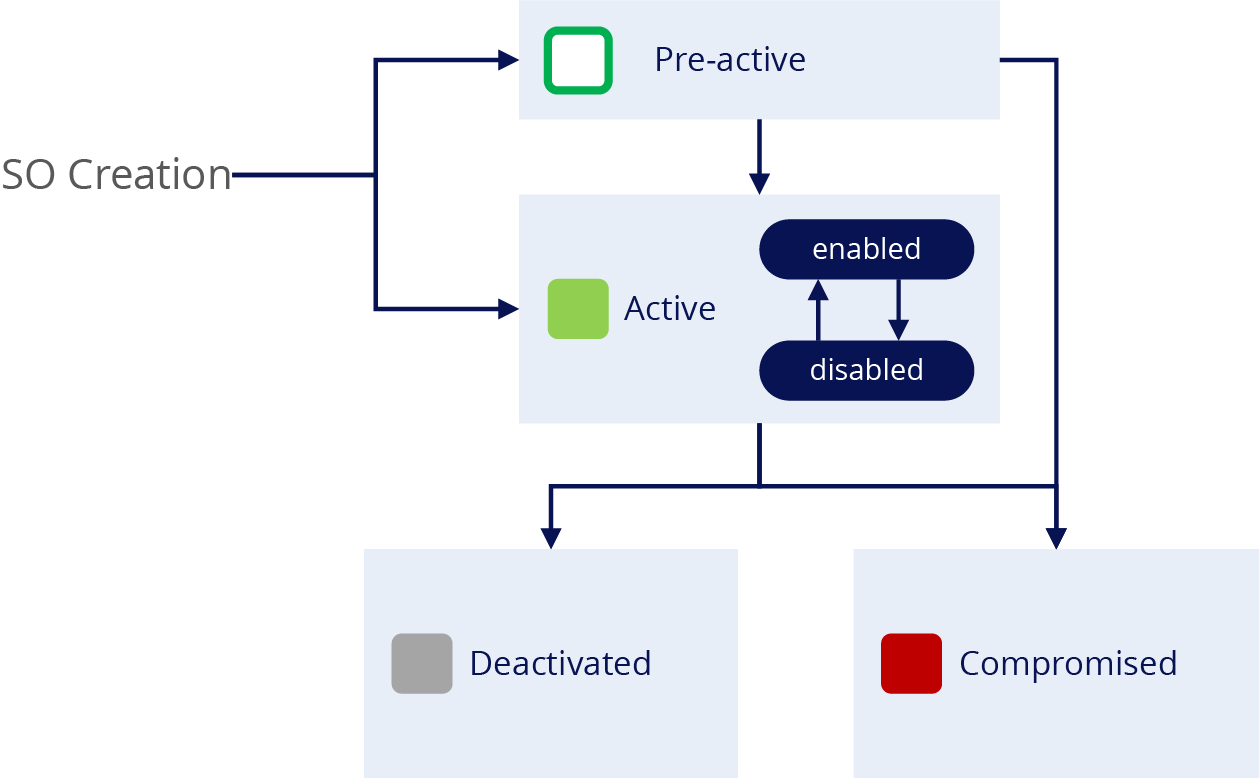
User S Guide Fortanix Data Security Manager Key Lifecycle Management Fortanix
Cryptocell Hardware Security Subsystem

Exploring The Lifecycle Of A Cryptographic Key
Breathing New Life Into The Customer Lifecycle

What Is Certificate Management Ssl Certificate Management
What Is A Cryptographic Key Management System The Security Lifecycle Solution Mtg Ag
The Key Management Lifecycle The Falcon S View

Certificate Lifecycle Management Best Practices Encryption Consulting

Post a Comment for "Crypto Key Lifecycle"